With cyber threats evolving constantly, IT teams face immense pressure to safeguard data from malware, phishing, and insider threats. Microsoft’s Purview platform, equipped with a powerful DLP module, provides a proactive defence. Data Loss Prevention (DLP) is a security solution that helps prevent unsafe sharing and inappropriate transfer of sensitive data. DLP is utilized to protect and monitor sensitive data across both on-premises systems and cloud-based locations within our organizations.
This blog post tackles the critical issue of data security in Microsoft 365. With the ever-growing threat of cyberattacks, protecting sensitive information like social security numbers, credit card data, and “Confidential” documents is paramount.
Microsoft Purview’s DLP module offers a powerful solution to address this challenge. We’ll delve into its importance and provide a step-by-step guide to configure a DLP policy that meets your specific needs.
Scenario:
Block all external sharing of SharePoint and OneDrive items containing sensitive information like Social Security Numbers Credit Card Data etc. and Sensitivity labelled item.
Alerting the Email notification to the security team for every blocked file sharing attempt. User notifications within the interface (if available).
By following our guide, you can gain control over sensitive data sharing and confidently navigate today’s complex cybersecurity landscape.
Step-by-Step Guide to Creating a DLP Policy in Microsoft Purview
This guide walks you through creating a Data Loss Prevention (DLP) policy in Microsoft Purview to prevent accidental or unauthorized sharing of sensitive data in SharePoint and OneDrive.
Step 1: Access the Compliance Portal:
Go to the Microsoft 365 Admin Center and navigate to “Compliance.”In the left-hand pane, find “Data loss prevention” and then “Policies.”
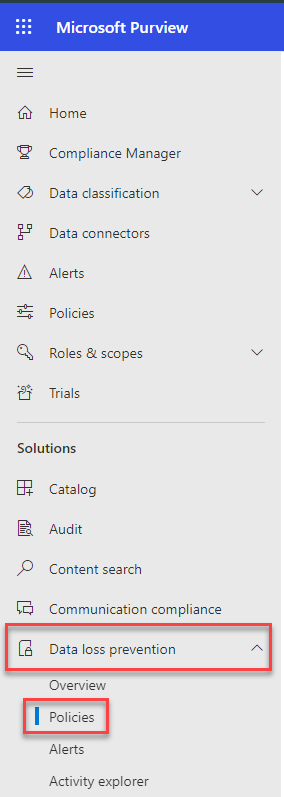
Step 2: Create a New Policy:
Click the “Create policy” button.
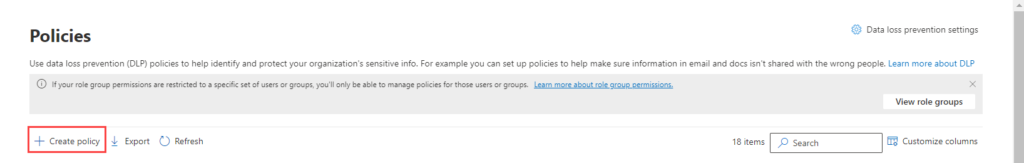
Step 3: Define Policy Details:
Under “Categories,” choose “Custom.” Under “Regulations,” select “Custom policy.”
Click “Next” to proceed. Give a proper policy name and description.
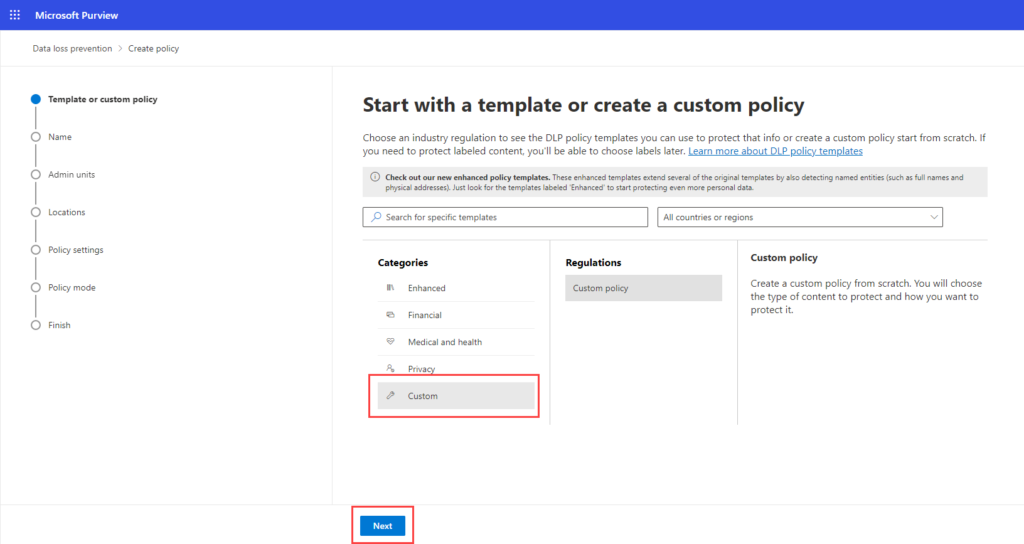
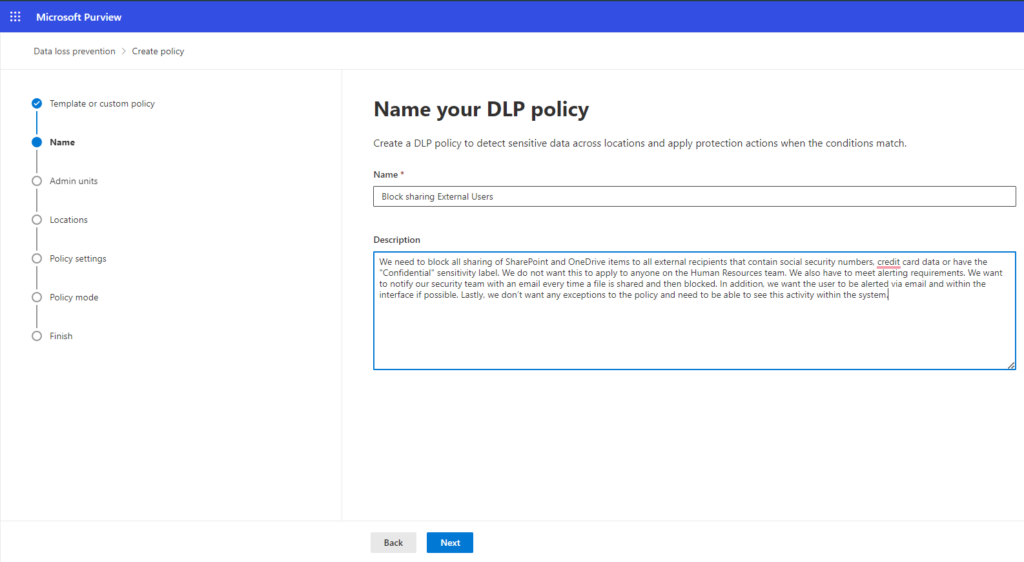
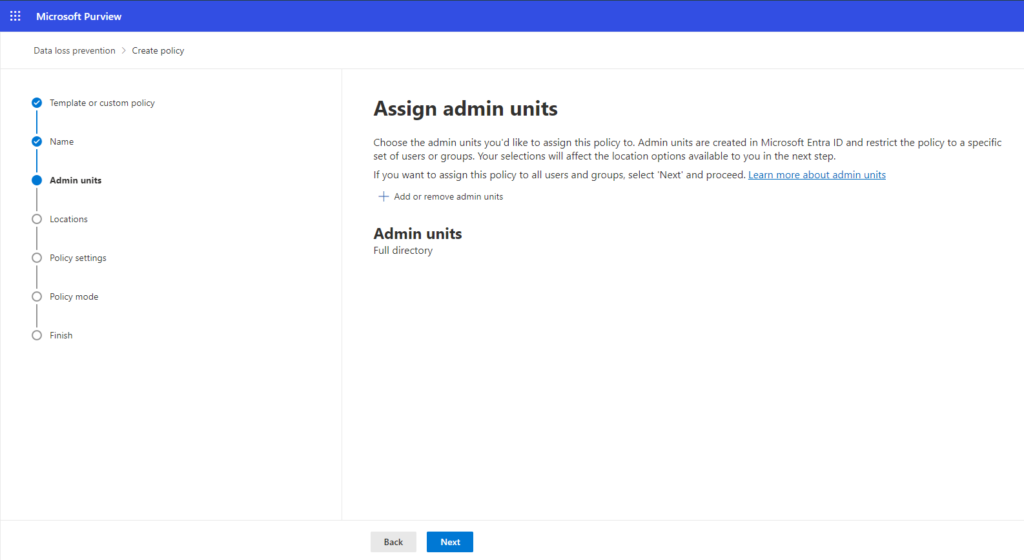
Step 4: Assign admin units for users or groups:
Similar to the default template approach, assign admin units from Microsoft Entra ID to limit the policy to specific users or groups.
Step 5: Enable DLP for SharePoint and OneDrive:
Turn on DLP for “SharePoint sites” and “OneDrive accounts.” Leave other locations disabled. Click “Next.”
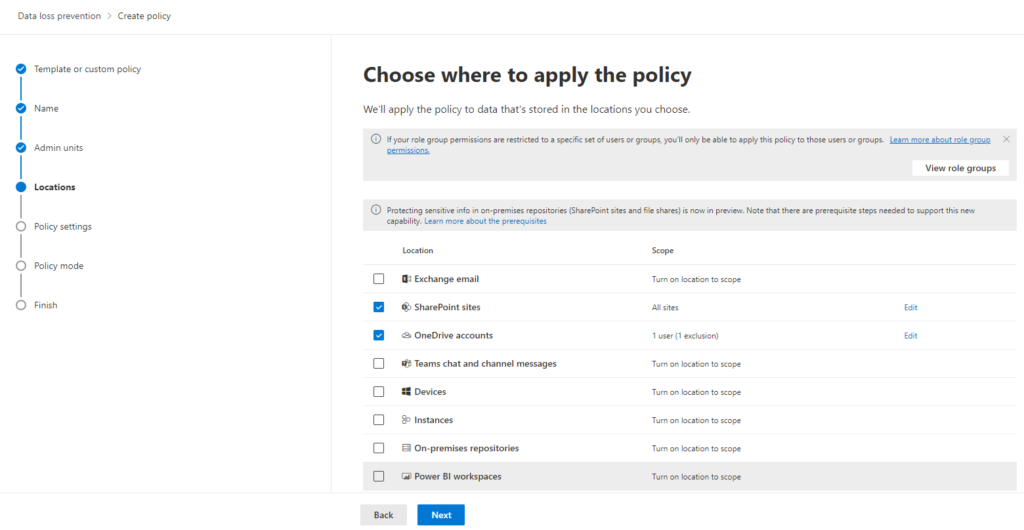
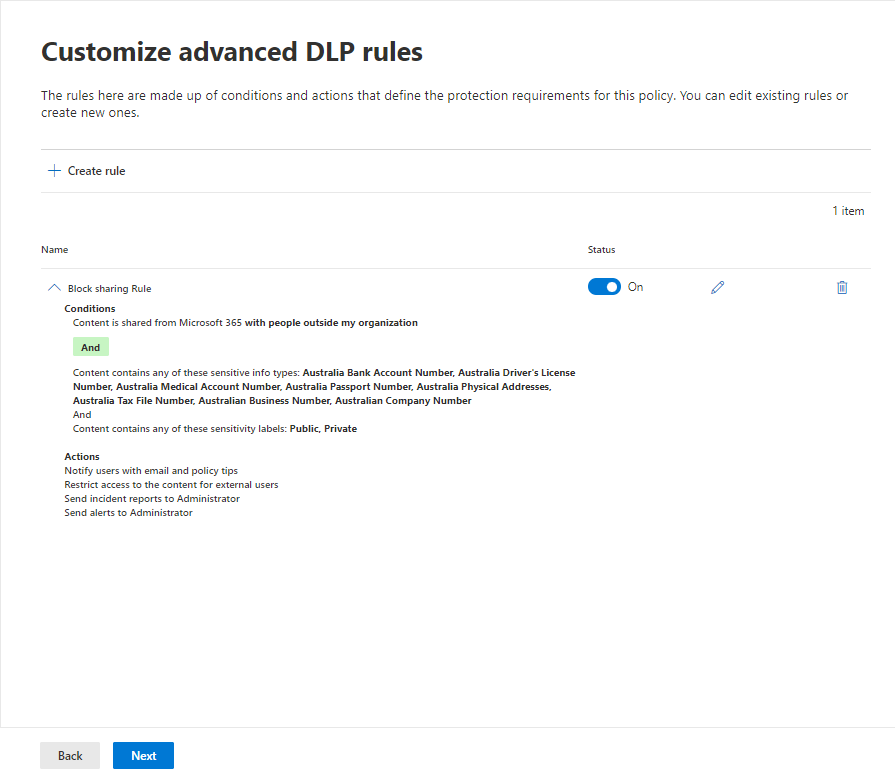
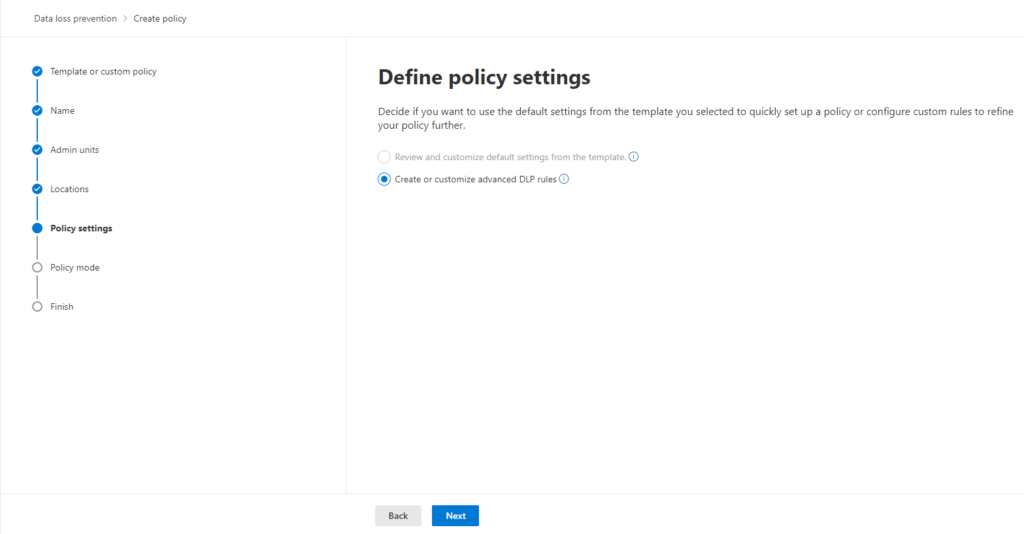
Step 6: Create and Define DLP Rule:
In “Define policy settings,” ensure “Create or customize advanced DLP rules” is selected. Click “Next” and then “Create rule.”
Give your rule a clear name (e.g., “Block External Sharing of Sensitive Data”). Briefly describe the rule’s purpose.
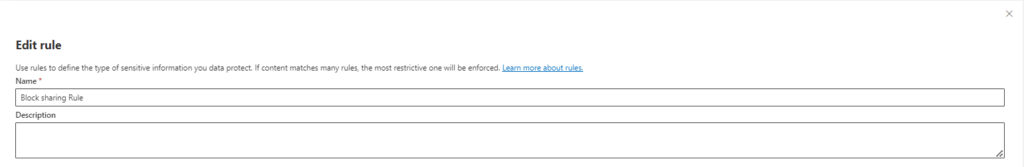
Step 7: Set Rule Trigger Conditions:
Click “+ Add condition”. Choose “Content is shared from Microsoft 365.” Select “with people outside my organization.” Choose “Content contains” and choose appropriate data types based on your needs. In this case, we’ve selected for sensitive Australian information such as credit card numbers, passport numbers, etc.
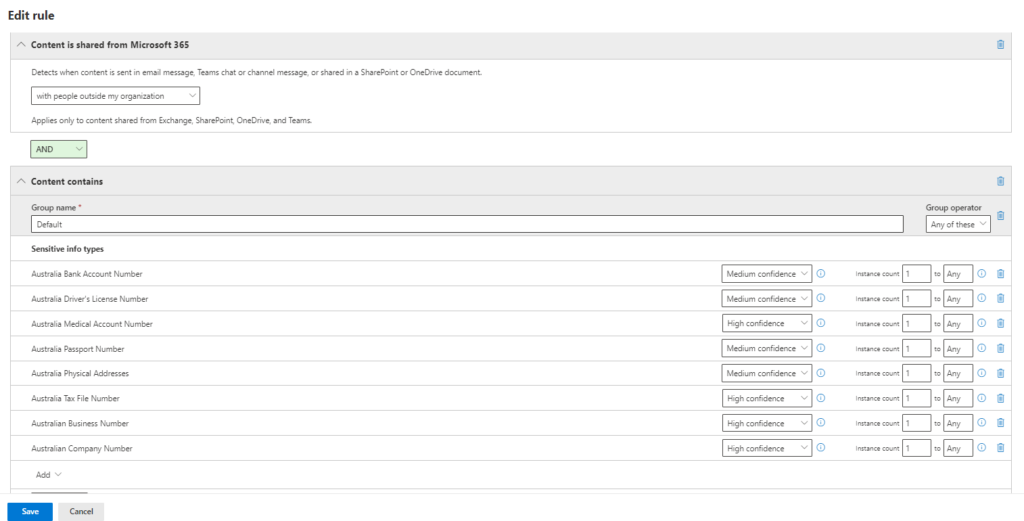
Step 8: Identify Sensitive Data:
Click “+ Add condition” and set the logic to identify content matching both conditions (AND). Create a new condition group with OR logic (matches at least one condition. Create a new condition group with AND logic (matches at least one condition). Choose “Sensitivity labels” and select the labels based on your needs.
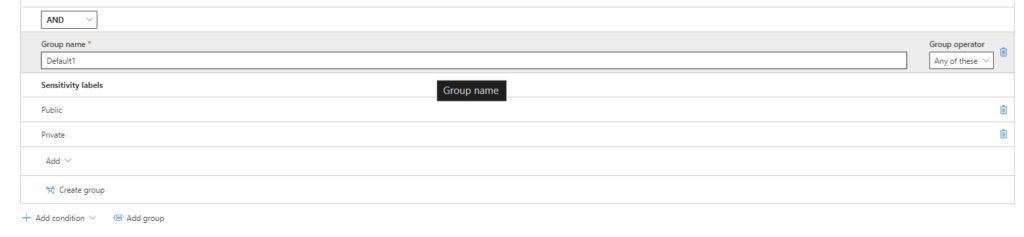
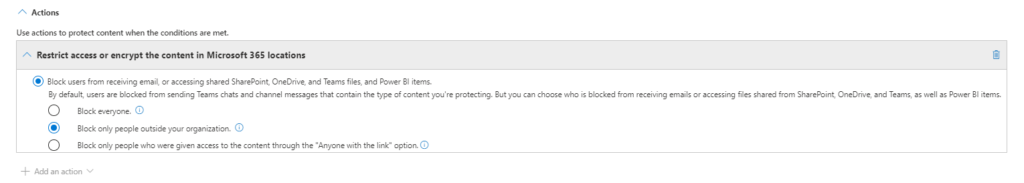
Step 9: Block Unauthorized Sharing:
Under “Actions,” choose “Restrict access or encrypt the content.” Select “Block only people outside your organization” to prevent external sharing.
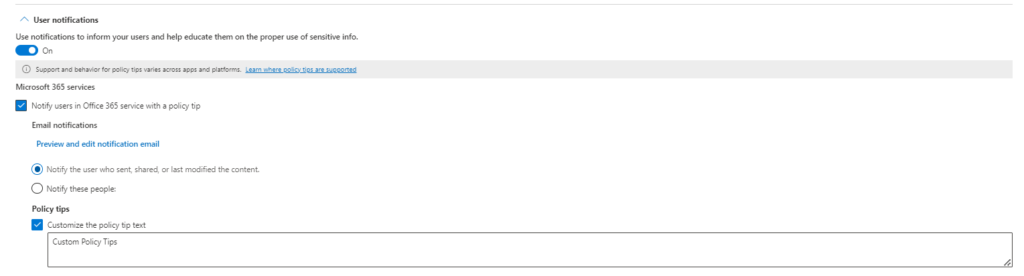
Step 10: Notify Users:
Enable “User notifications” to inform users attempting to share sensitive data through a policy tip in Office 365 services. This will notify the user who shared the data.
Step 11: Prevent Sharing Overrides:
Ensure “Allow override from M365 services” is not selected to prevent users from bypassing the policy.
Want to talk?
Drop us a line. We are here to answer your questions 24*7.