
Looking to Safeguard Crucial Info Within Microsoft 365? Dive into the Power of Sensitivity Labels! Explore how these labels protect data, enhance security, and drive productivity within Microsoft 365.
In today’s business landscape, safeguarding sensitive data within platforms like Microsoft 365 stands as a critical priority. The constant evolution of threats emphasizes the need for robust solutions like sensitivity labels. These labels not only categorize data but also fortify it against potential breaches while ensuring uninterrupted workflows.
Table of contents
- What is sensitive data?
- Securing data with sensitivity labels through Microsoft Information Protection (MIP)
- Configurable Label Settings: The label scope determines which settings can be configured within a given label, defining the breadth of its protective capabilities.
- Visibility to Users: It also governs where the sensitivity label will be visible to users, ensuring the seamless application of data protection measures.
- Assign Permissions Now: This empowers administrators to precisely designate user permissions for labelled content, offering meticulous control over access.
- User-Assigned Permissions: Opting for this allows users themselves to assign permissions when applying labels, fostering flexibility in collaboration while maintaining security protocols.
- Adding a Watermark: This embeds a visible layer of identification, reinforcing the ownership and sensitivity of the content.
- Including a Header: A content header provides contextual information and further enhances content identification.
- Appending a Footer: Similarly, a footer complements the content by offering additional identification and context.
- Privacy and external user access settings
- External sharing and conditional access settings
- Public Access
- Private Access
- None (Customizable Access)
Understanding Sensitive Data
As businesses navigate an increasingly digital landscape, safeguarding sensitive information is non-negotiable. Sensitivity labels, embedded within Microsoft 365, offer a powerful defence against evolving cyber threats. Striking the delicate balance between security and productivity, these labels pave the way for a future where data protection is proactive, efficient, and integral to business operations.
What is sensitive data?
Sensitivity labels are a vital component of data protection strategies. They categorize information based on its confidentiality, ensuring appropriate handling and access control.
Type of sensitive data?
Sensitive data encompasses various forms, including personal, financial, or proprietary information, demanding heightened security measures.
Importance of protecting sensitive data
The implications of data breaches can be severe, ranging from financial loss to reputational damage, underlining the criticality of safeguarding sensitive information.
WHAT ARE SENSITIVITY LABELS USED FOR IN M365?
When it comes to safeguarding sensitive data, WHAT ARE SENSITIVITY LABELS USED FOR IN M365? holds the key. These labels play a pivotal role in tagging data and implementing diverse protective measures. Let’s explore the multifaceted uses and security applications of sensitivity labels within the Microsoft 365 suite.
Understanding Sensitivity Labels
Sensitivity labels serve as crucial identifiers, enabling organizations to categorize data based on its sensitivity level. This categorization facilitates robust auditing and reporting mechanisms.
Labelling Content for Security
One primary function of sensitivity labels is to tag content, allowing for easy identification of its sensitivity level. This tagging system is pivotal for effective auditing and regulatory compliance.
Encryption for Content Protection
To prevent unauthorized access, sensitivity labels facilitate encryption, ensuring that only authorized users can access and decipher the content. This robust security measure mitigates the risk of data breaches.
Applying Content Markings
Incorporating content markings, such as headers, footers, and watermarks like ‘Confidential,’ further fortifies the security of sensitive data. These markers serve as visual cues, signalling the sensitivity of the information.
Protecting Content in Office and Third-Party Apps
Sensitivity labels aren’t limited to Microsoft’s native applications; they extend their protective reach to third-party apps like Salesforce, Box, or Dropbox. This broad compatibility ensures a holistic safeguarding approach.
Managing Containers in M365
Efficient management of containers, including Teams, Microsoft 365 Groups, and SharePoint sites, is achievable through sensitivity labels. This feature bolsters data security within collaborative platforms.
Securing Meetings and Chats
Sensitivity labels bring a layer of security to meetings and chats by allowing labelling and optional encryption of invitations and responses. Teams-specific options further reinforce security protocols.
Extending Labels to Power BI and Purview Data Map
Innovatively, sensitivity labels transcend beyond conventional applications, extending their protective umbrella to Power BI and Microsoft Purview Data Map. This extension ensures data protection across diverse services.
Steps to Expertly Set Up Your First Label in Microsoft: A Comprehensive Guide
Setting up sensitivity labels is crucial for data security. Understanding these labels and their significance lays the foundation for robust data protection.
Understanding Sensitivity Labels
Sensitivity labels are metadata tags applied to documents or emails to control access. They offer various functionalities like encryption, watermarking, and more.
Importance of Sensitivity Labels
Their role in securing sensitive information cannot be overstated. Effective labels ensure data confidentiality, integrity, and availability.
Types of Sensitive Information
Diverse data categories exist, from financial details to personally identifiable information (PII). Identifying the type of information is pivotal.
Creating Your First Label
Initiate the process by crafting the label itself, defining its functionalities, such as applying headers, footers, watermarks, or encryption.
Label Policy and Targeting
Understanding label policies and their role in targeting users, groups, or sites ensures the right data protections are applied to the right content.
Targeting Users/Groups/Sites
Delve into the process of applying labels to designated users, groups, or sites, ensuring comprehensive coverage.
Publishing Labels
Implementing labels across the organization requires a strategic and careful approach to ensure seamless integration and functionality.
Label Management and Updates
Maintenance and updates are crucial in ensuring label efficiency and relevance over time, avoiding obsolescence or security gaps.
Setting up your first label involves a comprehensive understanding of sensitivity labels, meticulous planning, and strategic implementation. Prioritize data security through effective label deployment and management.
How to Create and Define Sensitivity Labels in Microsoft Purview
Here, we’ll delve into the meticulous process of creating and defining these labels, empowering you to safeguard your data effectively.
Step 1: Navigating to the Compliance Centre
To initiate the creation process, begin by accessing the Compliance Centre within Microsoft Purview. Navigate through Information Protection and proceed to ‘Create New Label.’
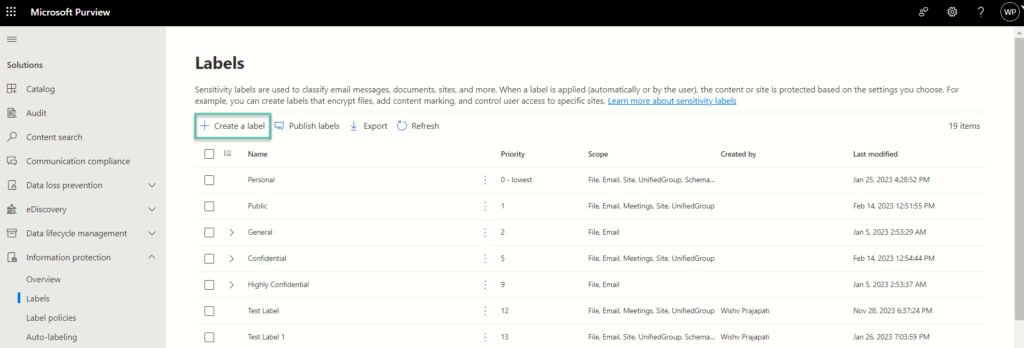
Step 2: Crafting Label Details and Description
Once within the ‘Create New Label’ section, meticulous attention to detail becomes paramount. Begin by entering fundamental information and crafting a descriptive overview for the label. Enter the fundamental information input, including Label Name, Display Name, Priority, and the comprehensive Description for both users and administrators, forms the crux of this phase.
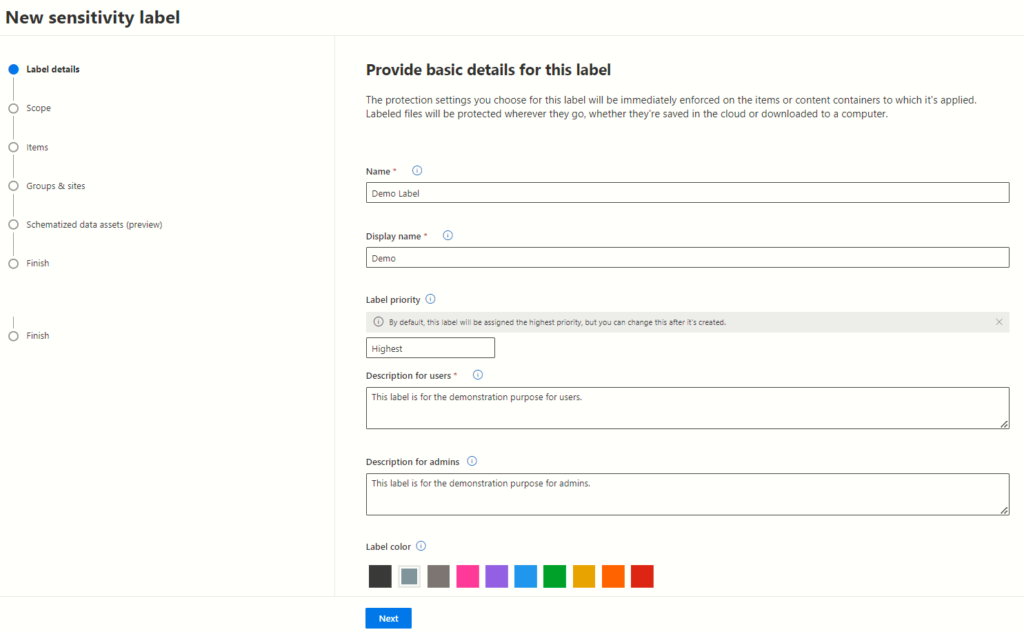
Understanding Label Scope and Configuration in Microsoft 365
These labels not only determine the parameters for data sensitivity but also dictate where and how these settings will be visible to users across diverse Microsoft 365 containers.
Configuring diverse sensitivity label configurations within the Microsoft 365 compliance centre is paramount in today’s data-driven landscape. Understanding and leveraging the label scope functionalities – Files & Emails, Groups & Sites, and Azure Purview Assets – empower organizations to fortify data security across various levels and containers.
Exploring Label Scope
The label scope embodies the essence of sensitivity labels within Microsoft 365. It holds the key to two critical elements:
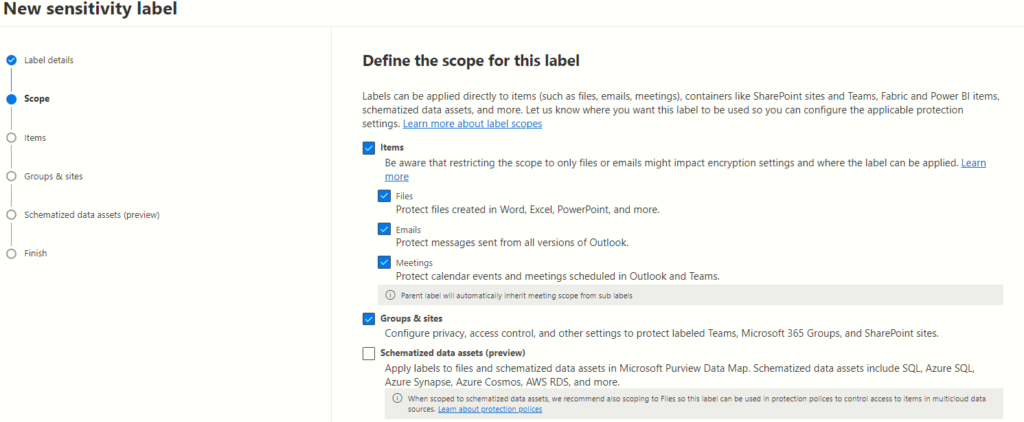
Configuration Options
Microsoft 365 offers various configuration scopes catering to distinct needs:
Files & Emails Scope
The foundational scope, “Files & Emails,” serves as the bedrock of sensitivity labels. It encompasses settings to encrypt, mark, and protect labelled emails and Office files. This scope, selected by default, empowers users to configure encryption and content marking for documents and emails effortlessly.
Interestingly, no additional licensing is required to configure settings within the “Files & Emails” scope, making it easily accessible to users by default.
Files & Emails Scope Functionality: This scope primarily deals with encrypting and content marking for documents and emails, aligning with the traditional perception of sensitivity labels. By selecting the “Files & Emails” scope, users gain access to configuration settings that protect emails and documents effortlessly.
Groups & Sites Scope
Expanding beyond document and email protection, the “Groups & Sites” scope introduces a broader canvas for sensitivity labels. It allows configuration to safeguard content within Microsoft Teams sites, Microsoft 365 groups, and SharePoint Online sites.
This scope presents a distinct facet by enabling protection settings at the container level. However, it necessitates the activation of capability before configuring protection settings for groups and sites. Once enabled, this scope is also selected by default, enhancing the security umbrella across these containers.
Functionality of Groups & Sites Scope: In contrast, the “Groups & Sites” scope extends beyond individual documents or emails, focusing on the protection of containers such as Teams sites, Microsoft 365 groups, and SharePoint Online sites. The protection settings at this level include defining privacy (public or private) for team sites and groups, regulating external user access, managing access from unmanaged devices, and enabling external sharing from SharePoint sites (in preview).
Azure Purview Assets Scope
For a more comprehensive data security approach, the “Azure Purview Assets” scope steps into the picture. It extends sensitivity labels to assets within Azure Purview, encompassing SQL columns, files in Azure Blob Storage, and more. Once this feature is enabled, this scope, too, becomes the default selection for your tenant, fortifying security measures across diverse assets within Azure.
Securing Labelled Items: Customizing Encryption and Content Marking Settings
The intricacies of data protection involve not only encryption but also content marking settings. Understanding and customizing these aspects is crucial to ensure robust security measures within organizations.
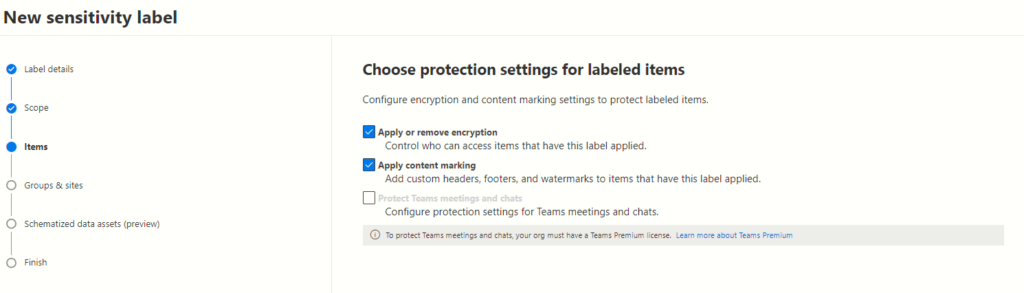
Click the next button to proceed to the next page,
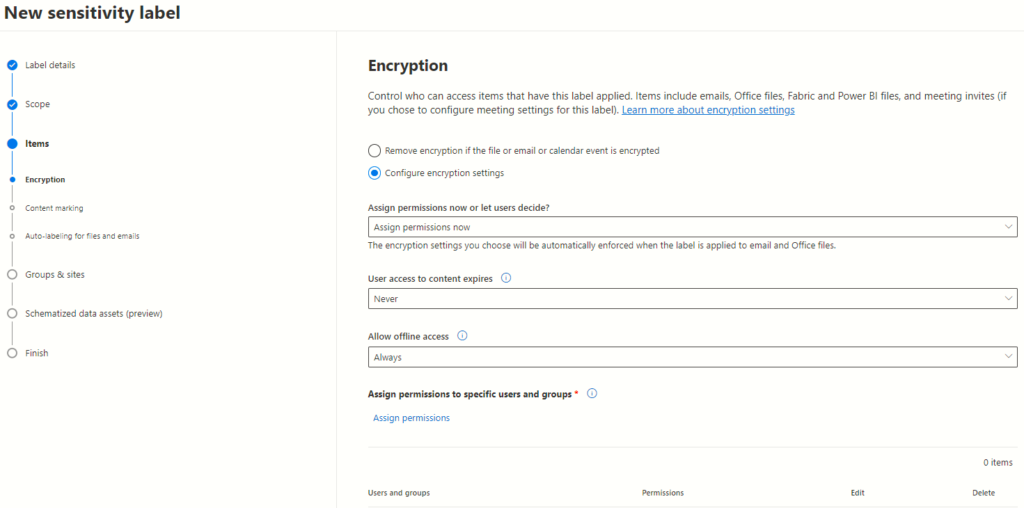
Configuring Encryption Settings
On the Encryption page, configuring sensitivity labels enables tailored protection. Two primary options present themselves:
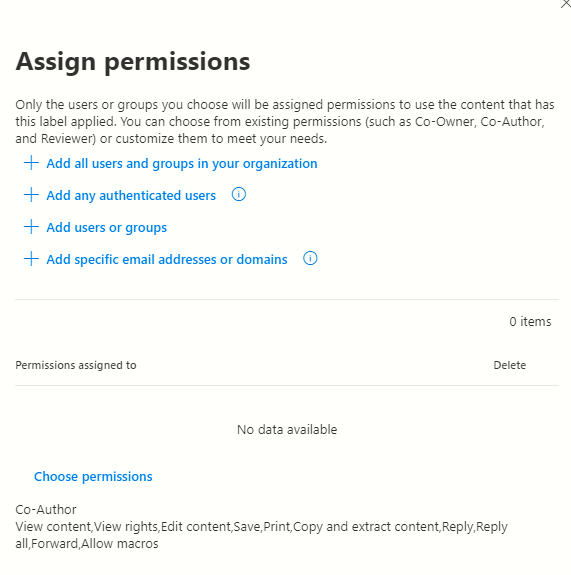
Assigning permissions to specific users or groups adds granularity to security measures. By individually designating permissions for labelled content, organizations fortify their data against unauthorized access.
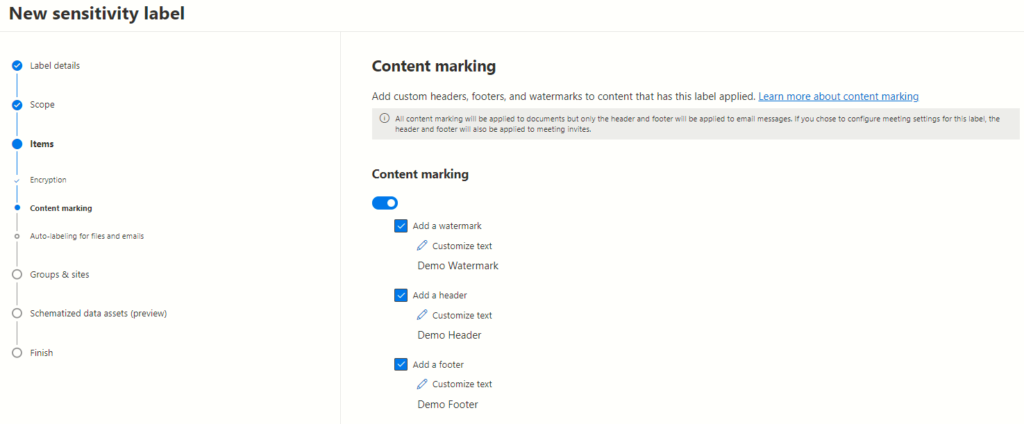
Content Marking Settings
Upon reaching the content marking page, three key options come into view:
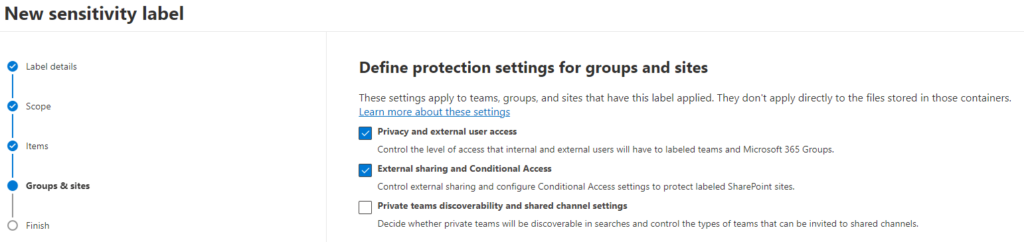
Protection Settings for Groups and Sites: Managing Access and Privacy
In today’s digital landscape, safeguarding sensitive information within collaborative platforms like Microsoft Teams and group sites is paramount. The control over access levels and privacy settings becomes crucial to ensure data integrity and confidentiality. Let’s delve into the intricate details of configuring protection settings for groups and sites, specifically focusing on privacy and external user access, as well as external sharing and conditional access settings. Select the ones that you want to configure the settings:
Understanding Privacy and External User Access Settings
Configuring Access Levels
When applying settings to groups, Microsoft Teams, or sites, administrators encounter pivotal decisions regarding access levels. The chosen settings significantly influence who can view, edit, and manage content within these collaborative spaces. The three primary options include:
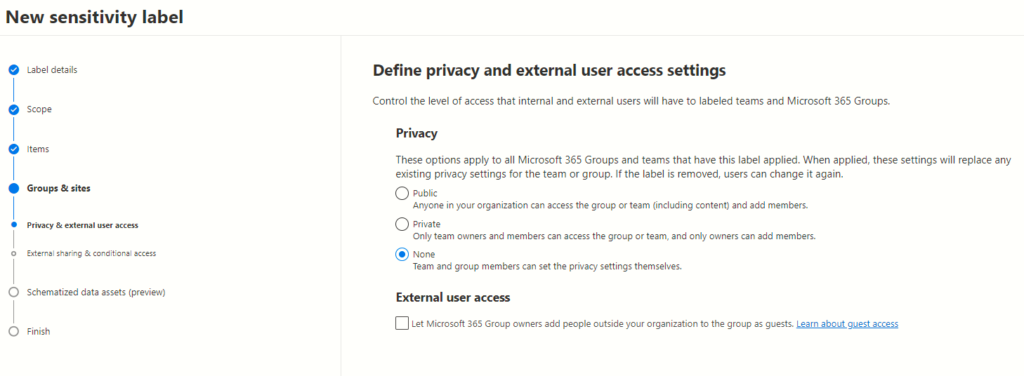
Managing Guest Access
Another pivotal aspect of privacy settings involves enabling or disabling group owners’ capability to add external users as guests. This feature, when enabled, permits external collaborators to access specific teams, sites, or groups based on predefined permissions. Administrators must weigh the necessity of external contributions against the risks associated with granting guest access.
External Sharing and Conditional Access Settings
Mitigating Risks through External Sharing Controls
Admins possess the authority to regulate external sharing of content and resources associated with labelled teams and sites. By defining stringent external sharing settings, organizations can fortify their defences against data leaks or unauthorized access.
Conditional Access: Strengthening Security Measures
Conditional access settings act as an additional layer of defence, implementing specific criteria for accessing sensitive information. By establishing conditions such as device compliance, location, or user roles, administrators bolster the security posture of collaborative platforms.
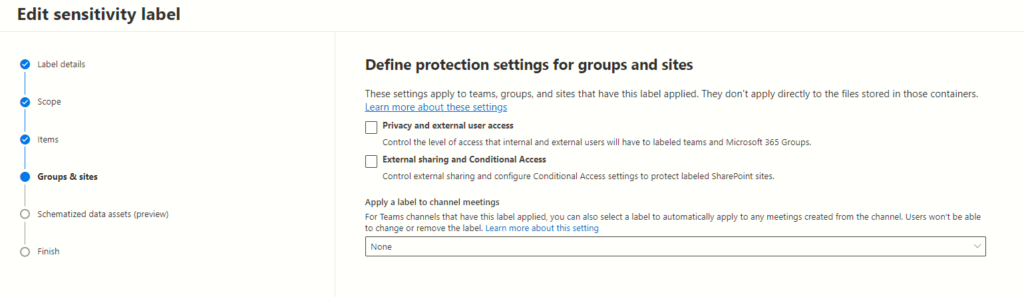
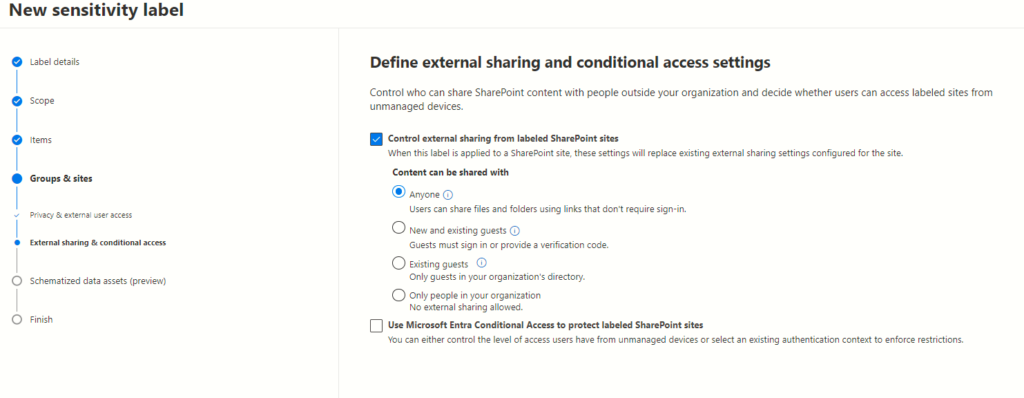
Enhancing SharePoint Security: Control and Protect Access Options
The next page presents two crucial options, each holding the power to fortify SharePoint sites: Controlling External Sharing and Leveraging Azure AD Conditional Access.
Understanding Control External Sharing from Labelled SharePoint Sites
Configuring External Sharing Settings
SharePoint administrators wield significant control over data sharing by configuring external sharing settings. This feature empowers them to dictate how content from labelled sites is shared with external entities. By opting for this setting, administrators can meticulously manage and monitor data accessibility beyond organizational boundaries.
Configurable Replacements for Existing Settings
The allure of this option lies in its ability to supplant existing sharing settings seamlessly. By configuring settings at the site level, administrators can override previous configurations, ensuring a more streamlined and secure sharing process.
Implications of Enabling Control External Sharing
Enabling this feature furnishes an added layer of control over data dispersion. It allows for a structured sharing environment, mitigating the risks associated with unauthorized external access while promoting seamless collaboration among permitted stakeholders.
Utilizing Azure AD Conditional Access for Enhanced Protection
Restricting Access from Unmanaged Devices
In a dynamic workspace, user devices vary in terms of management and security protocols. Leveraging Azure AD Conditional Access enables administrators to enforce restrictions on access from unmanaged devices, curbing potential security vulnerabilities stemming from these endpoints.
Authentication Context Configuration
One of the pivotal aspects of this option is the ability to configure authentication contexts. By setting stringent authentication parameters, administrators can elevate the security posture of labelled SharePoint sites, ensuring that access is only granted under specified and verified contexts.
Guide: Publishing Sensitivity Labels for Organizational Access
To commence this procedure, start by returning to the labels tab within the information protection settings housed in the Microsoft Purview Compliance portal. Here, the initial step involves selecting the specific sensitivity label intended for wider accessibility.
Once the intended label is identified, the subsequent action involves clicking on the conspicuous “publish label” button, conveniently located in the right panel of the interface. This simple act initiates a wizard-like process for creating a sensitivity policy. It’s worth noting that this wizard mirrors the one experienced when generating a policy from the label policy tab, with the distinction that, in this instance, a sensitivity label is pre-selected.
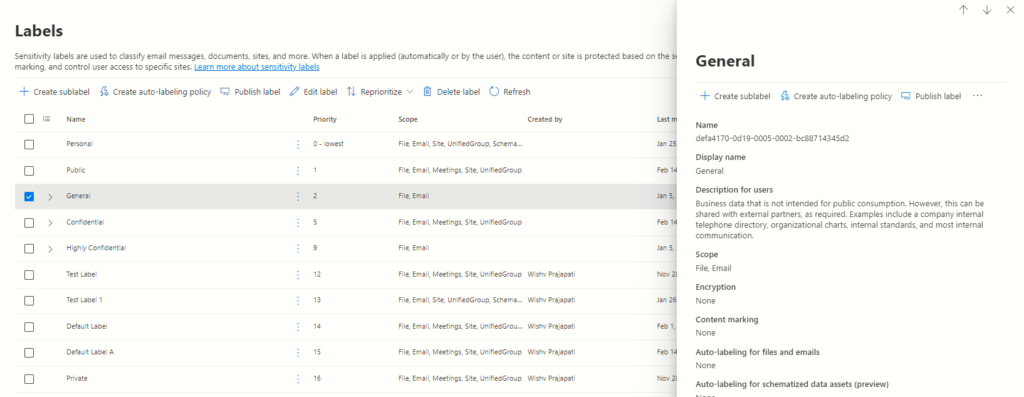
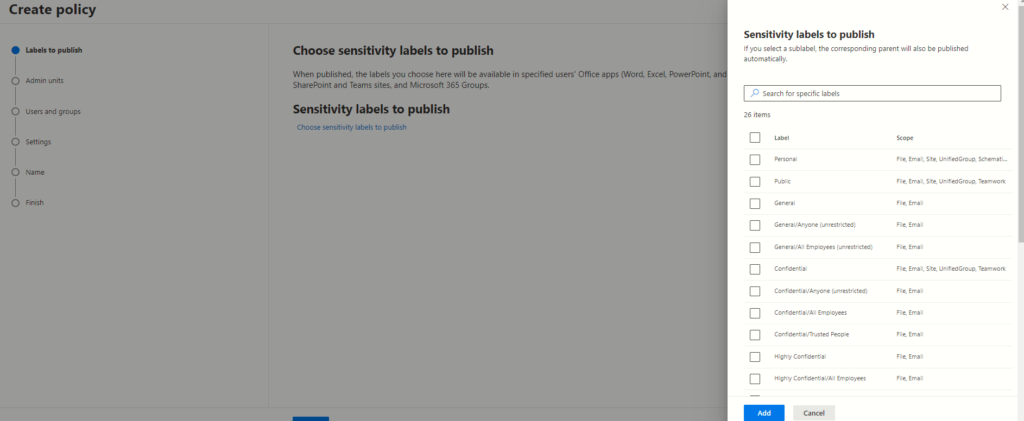
To advance to the following page, simply click on the “Next” button.
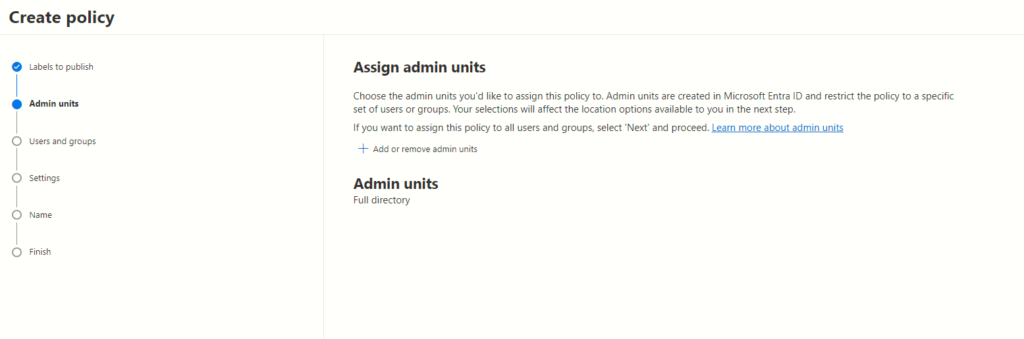
The selection of admin units plays a pivotal role. These admin units operate as the linchpin in restricting policies to specific user groups, significantly influencing subsequent location options. Understanding the nuances and functionalities of admin units is crucial for optimizing policy management within the Microsoft Entra ID ecosystem.
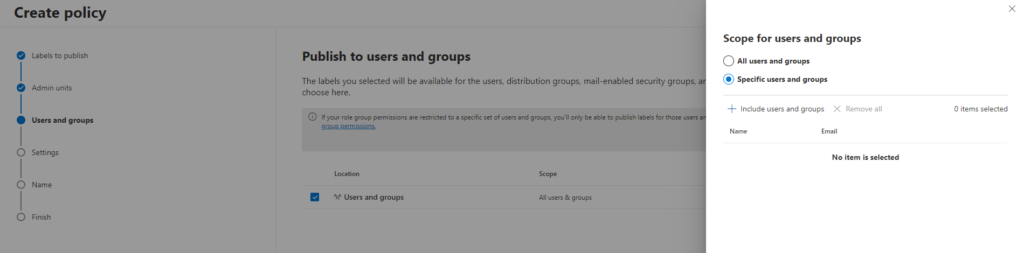
The upcoming page provides the option to define the users and groups targeted by the policy.
By default, it encompasses all users and groups. However, you have the ability to select particular users or groups by clicking the “choose user or group” link.
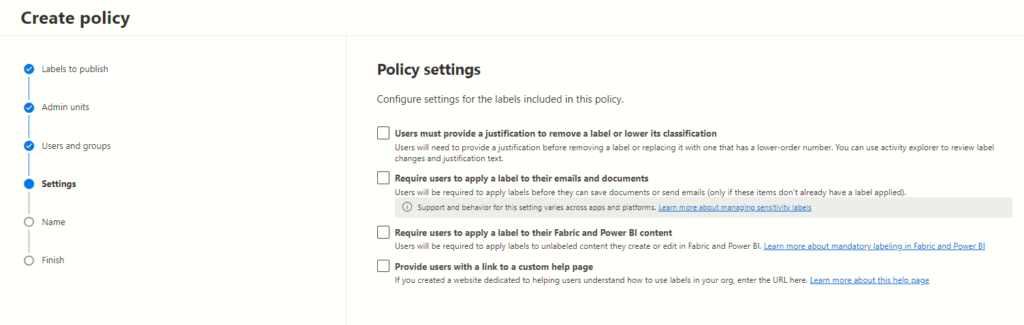
The Following Section: Policy Settings for Enhanced User Control
The upcoming policy settings delineate a spectrum of choices, allowing administrators to configure the system to align with organizational data security needs.
The Power of Choice: Exploring Policy Settings:
Enabling User Justification for Label Alteration
Granting users, the ability to provide justifications for label adjustments is a strategic move. By allowing users to articulate reasons for label modification or classification reduction, it fosters accountability while maintaining flexibility. This empowers users to engage responsibly with sensitive data, balancing their needs with organizational security protocols.
Mandating Sensitivity Labels for Email and Document Handling
One powerful setting involves enforcing sensitivity labels before sending unmarked emails or saving sensitive documents. This proactive measure ensures that crucial information is appropriately labelled, minimizing inadvertent data exposure. By mandating label application, users become conscious custodians of sensitive data, fortifying organizational data security.
Extending Sensitivity Labelling to Power BI Content
Incorporating sensitivity label requirements for unclassified Power BI content amplifies data protection strategies. With this setting, unlabelled Power BI content is no longer overlooked. Users are prompted to apply sensitivity labels, fortifying the integrity and confidentiality of insights gleaned from such data.
Custom Help Pages: Empowering Users with Guidance
The provision to showcase a custom help page offers invaluable guidance. Administrators can curate informative resources tailored to assist users in navigating sensitivity label application seamlessly. This fosters user proficiency and understanding, elevating the efficacy of data security practices within the organization.
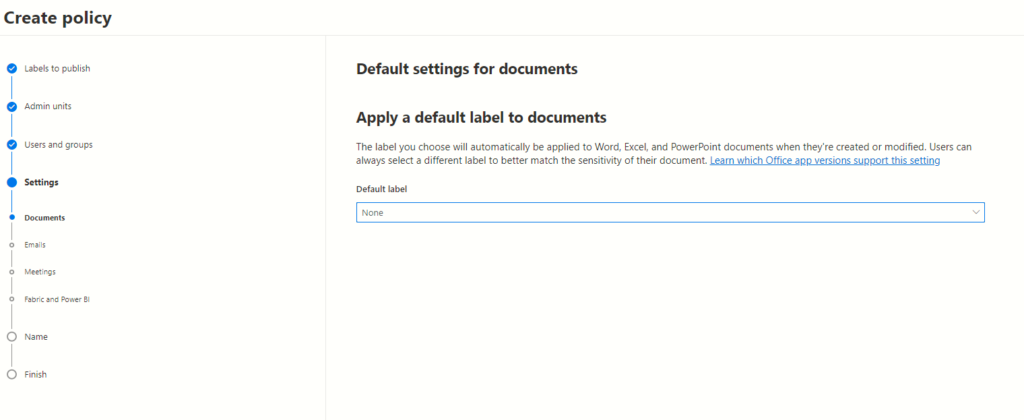
Default Label Assignment across Platforms
The subsequent pages usher administrators into assigning default labels across a diverse spectrum, covering documents, emails, meetings, sites, groups, and Power BI. This pivotal step streamlines the process, ensuring uniformity and adherence to organizational data classification standards.
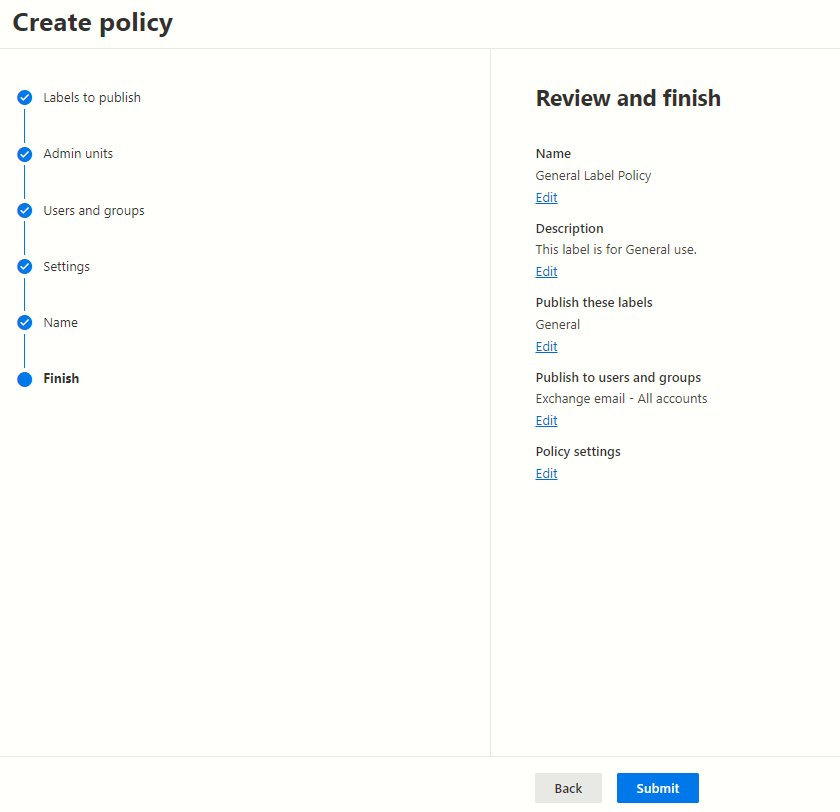
Examine and finalize the policy
Following this step, you’ll be prompted to name your new label policy. You have the option to include a description, although it’s entirely up to you; you can choose to leave it empty. After creating your initial sensitivity label, you’ll have the opportunity to review all aspects of the new policy. Once you’ve confirmed all the settings and particulars, proceed by clicking the submit button to complete the process.
Overview
Sensitivity labels are the modern shield for your organization’s data. They fortify your information against threats while nurturing a culture of responsible data handling. With seamless collaboration and robust protection, they ensure sensitive information stays safeguarded. Embrace sensitivity labels to proactively defend your data against evolving risks while fostering a secure, collaborative work environment.
Want to talk?
Drop us a line. We are here to answer your questions 24*7.



